E-commerce has come a long way. Online shopping experiences are rich and sophisticated, curated with acute attention to each step in the purchasing journey. Yet, shopping cart abandonment rates continue to top out at 69%. Many e-commerce leaders are left scratching their heads. Why they ask themselves, are so many people leaving without buying when we’re in a continuous cycle of enhancing the customer experience? Several components have been put in place to maximize conversion rates. Videos have been added to help tell the story. Image libraries, product recommendation engines, and online chat capabilities drive the purchase decision. CRM tools and shopping cart tech are upgraded. Advanced analytics help to spot trends and make adjustments on the fly. So, why aren’t we hitting revenue targets?
These tools that fuel the online shopping experience are important and beneficial, but in most cases, they aren’t coded or maintained by your in-house teams. Instead, they’re developed and operated by vendors, and therefore not within your control. This third-party codeIn communications and information processing, codeIn commun... More makes the dynamic, optimized shopping experiences that your customers crave. With variances based on user devices, geography, browser history, customer profile, and more, third-party codeIn communications and information processing, codeIn commun... More makes it possible for a female millennial in New York City shopping for a business suit to have a different experience than a 40-year-old male in Tulsa buying golf attire. These custom experiences deliver the right message to the right person at the right time, and they’ve revolutionized how brands can drive revenue growth.
Third-Party Code is Everywhere
It makes up much more of the digital experience than executives realize. By scanning over 1 billion websites last year, we’ve found that 65 – 90% of the codeIn communications and information processing, codeIn commun... More on the typical consumer-facing website are provided by third parties. That’s a significant amount of codeIn communications and information processing, codeIn commun... More outside of a site owner’s control.
The truth is that, when third-party codeIn communications and information processing, codeIn commun... More isn’t managed properly, digital revenue, reputation and brand loyalty suffer. Third-party codeIn communications and information processing, codeIn commun... More is critical to the shopping experience, but it could also be:
- Exposing your customers to ads that redirect them before they purchase
- Leaking data to competitors on customer preferences and shopping interests
- Stealing customer data such as credit card info, email addresses or other private info
- Causing customer frustration by making your digital properties load more slowly
Most companies won’t experience a critical data breach, but all digital executives must ask themselves: How does third-party codeIn communications and information processing, codeIn commun... More impact my customer experience and, therefore, my revenue? While trusted, verified third-party codeIn communications and information processing, codeIn commun... More can help make customers safer and more loyal, unknown third-party codeIn communications and information processing, codeIn commun... More outside of your control can introduce new risks or heighten existing ones, such as:
- Your risk for customer information theft and journey hijacking
- Your risk for customer data leakage
- Your risk for site latency
You can’t reduce these risks without understanding how the roles that codeIn communications and information processing, codeIn commun... More you don’t own or operate plays in the shopping experience. That means knowing the effects of third-party codeIn communications and information processing, codeIn commun... More on consumers who access your site using their devices, i.e., client-side codeIn communications and information processing, codeIn commun... More execution. With insights into which codeIn communications and information processing, codeIn commun... More does what to consumers’ devices, brands can derive more benefits from and mitigate the risks of third-party codeIn communications and information processing, codeIn commun... More. It’s a win-win situation. An effective digital risk scan will pinpoint these risks to help you reduce digital revenue threats like customer information theft, data leakage, and latency issues.

Customer Information Theft and Journey Hijacking
Imagine a shopper browsing products in-store, only to be taken by the arm and guided down a hallway to a different store. Implausible in the brick and mortar world, this happens regularly online when third-party codeIn communications and information processing, codeIn commun... More causes users to see competing for pop-up ads while they browse sites. Ads can even appear to be part of the overall site experience, causing confusion, distraction, and lost sales. For example, if a customer is about to check out but is shown an offer for 30% off and free shipping elsewhere, they may abandon their shopping session.
Because third-party codeIn communications and information processing, codeIn commun... More is rendered on the client-side, digital executives are often in the dark about their risk. To get a clear picture, digital executives need to know:
-
What JavaScript is rendering on my user devices, and where is it coming from?
Digital executives don’t realize how much codeIn communications and information processing, codeIn commun... More, typically JavaScript, is loaded from third-party domains. Market leaders utilize client-side scanning to show precisely which domains are loading JavaScript. By doing this, they can shield useful, necessary additional codeIn communications and information processing, codeIn commun... More from potential bad actors. Commonly, these bad actors put customers at risk by spreading malware through the digital supply chain.
-
Should any of these domains be blocked?
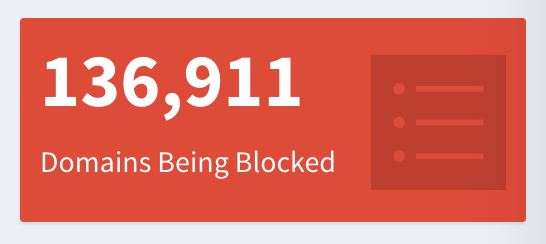
- Based on security or business rules some companies will choose to block certain domains from being called. With the average retail website utilizing more than 200 third-party domains, the key is knowing exactly which ones are compromising revenue. Access to a verified Digital Vendor Network with 15 years of history helps brands separate legitimate domains from ones that could be harmful to customers. For those domains you don’t recognize, it’s also important to have a partner that can work with third-party vendors to resolve security issues
.
Data Leakage
While third-party codeIn communications and information processing, codeIn commun... More could be hijacking customers in the here-and-now, there’s another, less apparent threat: data leakage through cookies and other tracking technology. When customers visit your site, they reveal their preferences and habits. By using tracking cookies, in-house teams can use these behaviours to enhance the shopping experience and grow revenue.
However, cookies dropped on your customers without your knowledge can collect your customers’ data to help your competitors market to them. Consumer intelligence resellers (e.g., agencies) rely on the results of your hard work hard to gain quality customers, and therefore they want it, too. They are aware that even after a sale is completed, a customer finding a better offer elsewhere is more likely to make a return. So, they use the information gathered on your website to do just that; entice a customer to make a return and shop somewhere else. As a result, not only do you experience a hit to your conversion rate, but your return on investment also takes a hit.
Cookies can be used by third-parties to take customer journey hijacking to the next level. In the past customers could be rerouted to a competitor while browsing your website, but today’s tracking cookies can help competitors and malefactors redirect customers even before they start browsing.
After scanning e-commerce sites for the past 15 years, we’ve seen it all. In fact, more than once we’ve seen Fortune 100 retailers plagued by ads from their top competitors just as their customer is in the process of completing a transaction. Cleverly, these bad actors know exactly when to target customers at the late stage of the online journey to take advantage of the investments to bring the customer to that point. Questions you should know the answers to include:
-
Who is dropping cookies on my site visitors?
Of the hundreds of third-party domains on a typical e-commerce website, many could be dropping cookies to gather data on your customers. The question is, who? And, are they using it to improve the experience or steal customers?
-
What data are they collecting?
Consumers readily or unknowingly exchange their information for a better digital experience. When third-parties misuse or abuse this personal data, your business will shoulder the blame, the reputational damage, the costs, and any topline losses. A digital risk scan assesses why cookies are dropped on your customers, if they add to core functionality, or if they potentially put them at risk.
-
Are my ordering and payment pages secure from data leakage?
Perhaps the most damaging way you can put customers at risk is not safeguarding their personal and payment details. For starters, there should be less third-party codeIn communications and information processing, codeIn commun... More on a payment page than the rest of your website.

Site Latency
Two seconds–that’s how little time you have to keep your customer engaged before they bounce off your website. Today’s consumers won’t wait for pages to load; they expect sites to load faster than they did three years ago. To make matters worse, those consumers aren’t likely to come back. Over half of online shoppers state that quick page loading is important to their site loyalty, and 79% of shoppers who are dissatisfied with website performance are less likely to buy from that site again. Leading retailers have performance tools in place, but the missing piece is client-side emulation that gives digital executives the complete picture of what your customers experience. A comprehensive scan answers crucial questions:

-
How “heavy” is the JavaScript on my site based on the average download size?
Large files mean long page load times. Pinpointing the domains and codeIn communications and information processing, codeIn commun... More that have the largest file sizes gives digital executives actionable intelligence on how they can improve the customer experience.
-
What’s the average latency in seconds that my users experience?
When third-party codeIn communications and information processing, codeIn commun... More powers your customer experience, it creates latency in page loads, adding a major speed bump to the shopping experience. This codeIn communications and information processing, codeIn commun... More resides on domains that your team doesn’t control, so it’s critical to understand the performance impact of codeIn communications and information processing, codeIn commun... More dependent on the third-party servers and their network connections.
-
What new domains are being called from my digital properties?
Third-party codeIn communications and information processing, codeIn commun... More isn’t static. It continuously changes, often legitimately, from functional enhancements and new relationships with digital vendors. In some cases though, they could be bad actors that represent a security risk or indicate codeIn communications and information processing, codeIn commun... More that will hijack the customer experience. Our analysis of major retailers shows that 30 – 60 new domains are called through third-party vendors within just a month.
Get Insights, Protect Your Revenue
You’ve devoted significant resources to create a powerful e-commerce experience. Let’s not allow security issues silently chip away at your revenue. With a free, comprehensive digital risk scan, you can take advantage of proprietary scanning technology to pinpoint the codeIn communications and information processing, codeIn commun... More disrupting your user experience. More than 600 retailers, media publishers, advertising and marketing technology providers, agencies, and enterprises rely on The Media Trust to protect their digital environment, their revenue and, most importantly, their brand. Request your digital risk scan today.









Leave A Comment