Understanding the Risk
Hidden Threats: What You Don’t See Can Hurt You
When it comes to securing email and protecting against
cyberattacks, most organizations focus their attention and
resources on inbound emails. They invest in strong email
security gateway solutions designed to thwart incoming
phishing attempts, malware, impersonation attacks, malicious
URLs and attachments and other content generally categorized
as spam.
This is a great start …
However, based on aggregate data of Mimecast customers, only
40% of email originates through inbound system traffic. The
other 60% of email traffic is introduced via internal-to-internal
(40%) or outbound (20%) email communications.
In other words, most companies are not inspecting and
securing up to 60% of their email traffic.
Emails sent between users or from internal users to third parties
such as customers and suppliers represent the majority of most
organizations’ email traffic; however, they are often left underprotected.
And as we’ve seen from past news events, it only takes
one successful attack to infiltrate an organization’s email
environment, leak sensitive information and cause longterm reputational damage.
Your Employees Can Be Your Greatest Asset, or Your Weakest Link When it Comes to Email Security
According to Mimecast’s 2018 State of Email Security Report, developed in conjunction with Vanson Bourne:
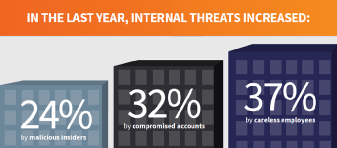
Employees frequently become unwitting participants in attacks, aiding the lateral movement of threats through the distribution of malicious URLS and attachments or the exposure of sensitive data.
Wwe’ll take a closer look into several
email-related activities that employees often engage in that contribute to the spread of these insider (“hidden”) threats and then discuss what measures your organization can take to protect itself from these “hidden” threats.


Bob, a finance manager is in a rush to finish fiscal planning for 2019. He is using two Excel spreadsheets to communicate with the sales leadership team around proposed targets for next year. One sheet includes employee names as well as current and proposed sales targets. The other sheet has the same information but also includes salary and bonus information for the entire sales organization. In a hurry, Bob accidentally forwards the more sensitive version of the file to the
entire leadership team via a distribution list. He notices his mistake right away but has no means to pull the email from the various users’ inboxes. Instead he calls all of them and begs them to delete the file. Unfortunately, Emily, the director of sales operations, is away from the office and opens the file. Emily notices she makes less money than those in her peer group. She is livid and HR and Emily’s boss, the SVP of sales, need to have multiple meetings with her to diffuse the situation.
Jennifer receives an email saying that there is an issue with her Microsoft Office 365™ account and she needs to login to her account to verify and update her information. The email was sent to her work email and Rima clicks on the link provided and proceeds to login with her Microsoft account credentials (typically Active Directory credentials). Unknown to Rima, the site she is on, while looking legitimate, is actually a phishing site set up to harvest her credentials as she attempts to “login” to Office 365. Not only do the attackers now have her login information, but they then quickly use it to gain access to
her Office 365 account and read her email correspondence and archives. They then use their access to her account to send emails, containing malicious links, malicious attachments and/or malware, to distribute an attack to all her contacts. These include internal colleagues as well as partners, many of whom consider Rima a trusted contact and click on the malicious link or open the attachment
in the email. The threat continues to spread like wildfire both within Rima’s organization and within her partners’ organizations.
Minimize Damage to Corporate Brand
Clearly, once Jennifer’s partners realize that the email they received from her was indeed malicious, they may feel violated. No one wants to be connected to malicious activity, especially at a corporate level. There is a level of trust between partners, vendors and other third parties that sensitive data will be protected, and appropriate security measures will be taken to safeguard against compromises. Having such an event take place can leave a bad taste in a partner or vendor’s mouth and leave a long-lasting negative brand impression on the offending organization.
The Mimecast Difference
Mimecast can help provide reputational protection for your organization. Internal Email Protect scans all internal and outbound email traffic to help prevent the spread of attacks between internal users and to third parties like customers and suppliers, while also protecting against the unintentional or malicious exposure of sensitive information.



Maria has a friend who is interested in an open position at her company. Her friend sends his resume to Maria using Dropbox. Maria accesses the resume via Dropbox and saves it onto her work computer. She then attaches the file to an email that she then sends, using her work email account, to the HR recruitment lead for the position.
Scan Internally Distributed Attachments and Links
Your Content Goes Here
The HR recruiter opens the attachment, sees that there is a link to the applicant’s LinkedIn profile and clicks on it. Unfortunately, the resume Maria attached contains malicious codeIn communications and information processing, codeIn commun... More and by clicking on the link, has unleashed a virus on the recruiter’s computer that then infiltrates the organization’s network.



Bob, a finance manager is in a rush to finish fiscal planning for 2019. He is using two Excel spreadsheets to communicate with the sales leadership team around proposed targets for next year. One sheet includes employee names as well as current and proposed sales targets. The other sheet has the same information but also includes salary and bonus information for the entire sales organization. In a hurry, Bob accidentally forwards the more sensitive version of the file to the
Take Back Control with Remediation
The Mimecast Difference
Mimecast can help IT take back control by providing organizations with advanced message and threat remediation capabilities. Internal Email Protect can automatically reach back into a user’s inbox to remove infected or undesirable emails. Administrators can also manually monitor, search for and remediate emails via the Threat Remediation Dashboard.
entire leadership team via a distribution list. He notices his mistake right away but has no means to pull the email from the various users’ inboxes. Instead he calls all of them and begs them to delete the file. Unfortunately, Emily, the director of sales operations, is away from the office and opens the file. Emily notices she makes less money than those in her peer group. She is livid and HR and Emily’s boss, the SVP of sales, need to have multiple meetings with her to diffuse the situation.



Jonathan just found out from his boss that he will be let go from his organization. He has worked at his company for over seven years, pouring his blood, sweat and tears into numerous projects that have proven to be very successful and driven strong revenue growth over the years. The news of his imminent layoff has left him very angry, confused and hurt. He is so upset, he rushes back to his computer, and without thinking twice, he sends out an email with inappropriate language that is negative
DLP to the Rescue
The Mimecast Difference
Mimecast Internal Email Protect can help prevent accidental or intentional exposure of profanity, abusive language and/or confidential information by applying data leak prevention policies to internal and outbound emails. Internal Email Protect can also help to mitigate damage through automatic or manual removal of internal-to-internal emails.
about the leadership of the organization to all of his contacts. He also talks about the roadmap of the product he is working on and delivers a long rant about key features that he does not agree are a good idea but that the leadership team is insisting should be incorporated in the product. In addition to his work colleagues, some of the recipients of this email are partners, vendors and customers he has worked with over the years.


Threat protection, visibility and remediation for internal and outbound email
Arm Your IT Team with the Visibility it Needs to Protect Your Organization
Remediate Threats
Protect the Integrity of Your Organization
Internal Email Protect (IEP) prevents the spread of attacks between internal users and to third parties like customers and suppliers, while also protecting against the unintentional or malicious exposure of sensitive information.EBOOK FROM MIMECAST INTERNAL THREATS PERSONIFIED: HOW EMPLOYEES CAN JEOPARDIZE YOUR CYBERSECURITY










Leave A Comment